
It was only a few years ago when IT departments were able to manually handle vulnerabilities. Today, disruptive technologies and dynamic approaches to development have changed the digital landscape. Security is no longer the sole responsibility of the IT department. The borders of the security perimeter have been blurred, obscuring the visibility of digital spaces.
Into this dark and chaotic digital scene, enter Software Composition Analysis (SCA) systems. They are powerful and fearless in their quest to ensure each component in your codebase adheres to the policies you pre-defined. The SCA system scans your digital ecosystem and alerts you of the presence of intruders such as vulnerability and licensing issues.
Read on to learn what is Software Composition Analysis and how it can help you maintain a healthy codebase.
What Is Software Composition Analysis?
Software Composition Analysis (SCA) systems automate the process of gaining visibility into the components of a system. Organizations use SCA tools to create an inventory of the different types of code components—proprietary, third-party commercial and open source. Once you have an inventory, you can better manage the licensing and monitor vulnerabilities.
The Dangers of Open Source Components
The agile methodology, while flexible and efficient, has created immense pressure on Agile, DevOps, and CI/CD teams. With the goal to produce applications as fast as humanly (and machine-ly) possible, developers have adopted the use of open source (OSS) components. Instead of writing the codebase from scratch, developers can save a lot of time by using OSS as frameworks and templates.
The downside to using open source is its open nature - anyone with can access the code and modify it. That includes well-meaning but green programmers who can accidentally create a vulnerability—and savvy programmers with malicious intents set on intentionally creating a vulnerability.
Over 5,000 vulnerabilities were reported in the first quarter of 2019. While not all vulnerabilities present an immediate risk, many of them could wreak havoc on your system if left unattended.
Benefits of Software Composition Analysis
1. Automatically Track Open Source Components
Keeping track of all the exploitable ways through which an attacker can bypass the security perimeter is no longer humanly possible. Many organizations are left blind as to the exploitable state of their code. A frightening number of organizations fail to apply patches even after a vulnerability is discovered.
Software Composition Analysis tools automatically keep track of vulnerabilities, ensuring that human operators gain the visibility they need into the codebase. SCA tools provide Bill of Materials (BOM) functionalities for automated inventorying. Once the SCA finishes the static scan, you will get a detailed report that lists all of the detected vulnerabilities and information on dependencies and affiliated licenses.
2. Continuous Monitoring for Vulnerability Detection
In today’s fast-paced development landscape, static scanning is no longer enough to ensure your codebase is secure. Static scanning has its advantages, especially for checking your code before you release the software. However, once you release your code into the world it’s no longer as protected as it was in your safe and secure development environment.
A lightweight website that remains static for a long time can find itself the target of a dormant exploit. Applications that require constant updates could accidentally introduce a vulnerability if rushed into releasing without a proper scan.
Since there isn’t always time to run a static check, you can make use of an SCA tool that enables continuous monitoring. The SCA tool will send you alerts based on pre-configured triggers, ensuring that you always have visibility.
3. Automated and Prioritized Vulnerabilities Remediation
In the late 90s, when vulnerabilities averaged at 85 per month, a manual vulnerabilities assessment was enough to help IT departments secure their infrastructure. The last two decades have seen a steady increase in reported vulnerabilities, until, in 2017, a flood of vulnerabilities washed over the development landscape like a dangerous tsunami. Since then, each year has claimed a new record for security vulnerabilities.
The field of vulnerabilities management was introduced to help developers and security professionals gain control over the snowballing amount of vulnerabilities. Today, technology teams are expected to detect, report, prioritize, and remediate vulnerabilities, across all environments. Applications, containers, and clouds are as susceptible as IT networks and databases.
Advanced SCA tools provide automated vulnerabilities management tools throughout the entire pipeline. You can reduce false positives by setting up automated vulnerabilities prioritization. The SCA systems will send you real-time alerts with suggestions on how to remediate. Since all your systems are integrated, you’ll be able to automatically issue tickets to any member of your team.
4. License Risk Management
A software license is a legally binding agreement that defines the usage and distribution rights of the software. In the US, all software—except public domain software—is protected by copyright laws. There are many types of licenses, each grants its users different rights. License types are generally divided into two categories—propriety and free.
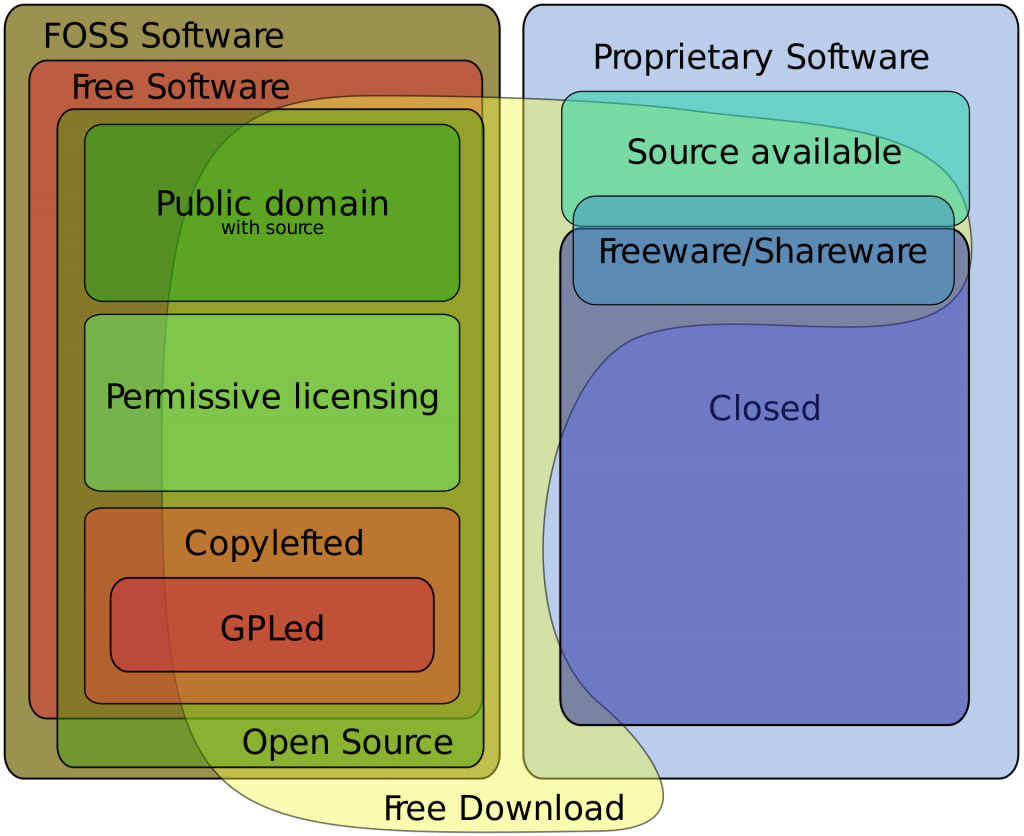 Image Source: Wikimedia Commons
Image Source: Wikimedia Commons
Software licenses protect all parties involved, ensuring that owners, creators, and users alike know how their rights. However, today’s codebase has become so fragmented, keeping track of licensing types can take a lot of time. There are over 200 open source license types, and not all grant the same rights. The consequences for violating OSS rights can be just as dire as violating propriety license rights, with one particular case costing the infringer $100 million.
SCA tools can help you lower the risks associated with licenses and compliance. You can create license policies with white lists and backlists, and configure the SCA system to automatically scan and alert you of any license issues. If you want to monitor all of your systems, you can integrate the SCA with your environments and set it up to continuously monitor the source code.
The Bottom Line
While open-source software is an indispensable resource for developers of all stripes, it is the very nature of open-source code that makes it especially vulnerable. If you can access it easily, so can malicious actors.
However, you can achieve an acceptable degree of security if you treat your open-source components with care. You can use software composition analysis tools to help maintain visibility over your components, as well as to discover and manage vulnerabilities.
With the automated capabilities of SCA, you can rest assured that it is possible to maintain healthy open-source management practices while keeping up with the fast-paced demands of your workload.


