What Is Endpoint Protection and Why is it So Important?
Endpoint protection tools and practices enable you to protect a network against endpoints and entry points, including desktops, mobile devices, and laptops. It aims to ensure that if any of these endpoints are compromised by malicious actors or campaigns, the rest of the network remains unaffected.
Initially, endpoint security evolved to cover the gaps left by traditional antivirus software, which relied on signatures to detect known threats. Today, endpoint security is a whole category of products that can monitor endpoints and entry points, identify threats, block suspicious activity, and respond to security incidents.
Endpoint security helps achieve visibility into endpoints, providing the capabilities needed to protect against sophisticated malware, evolving zero-day threats, and campaigns targeting endpoints as an entry point to breach the network. Depending on the vendor and your needs, you can deploy protection on-premises or use a cloud-based endpoint solution.
What is Microsoft Defender for Cloud?
Defender for Cloud is a tool for managing your security posture in Azure and protecting against threats. It is not an Azure-specific solution, and can also protect workloads running in hybrid environments, other cloud platforms, and for resources being migrated to Azure.
Defender for Cloud lets you harden cloud resources, track security mechanisms, prevent cyberattacks, and simplify security management. It is quick to deploy with automatic configuration that provides adequate protection for resources by default.
Defender for Cloud offers a limited free mode for all Azure subscriptions. Free mode provides a “secure score” for your workloads and lets you view security ratings, define security policies, and receive security recommendations for Azure resources.
If you choose to upgrade to a paid plan, Defender for Cloud can provide the following additional features:
- Microsoft Defender for Endpoint—comprehensive endpoint protection including endpoint detection and response (EDR).
- Vulnerability assessment—supports for virtual machines, container registries, and SQL resources. This feature can detect, manage, and remediate vulnerabilities directly from the Defender for Cloud interface.
- Multi-cloud security—lets you connect accounts on Amazon Web Services (AWS) and Google Cloud Platform (GCP) and use Microsoft Defender for Cloud to protect all cloud resources across multiple cloud providers.
- Threat prevention alerts—advanced behavioral analytics, combined with data from the Microsoft Intelligent Security Graph, helps identify unknown attacks and zero-day vulnerabilities.
- Container security—provides vulnerability management and real-time threat protection for containerized environments.
Working with Microsoft Defender for Cloud
Secure Score
Defender for Cloud provides a Secure Score for your entire cloud environment. It shows your current security posture at a glance; the higher the score, the lower the identified risk level. This helps you understand your current security situation and take action to improve it.
On the Azure portal page, the Secure Score is displayed as a percentage value, together with the number of unhealthy resources and the breakdown per cloud (if you are monitoring multiple clouds):
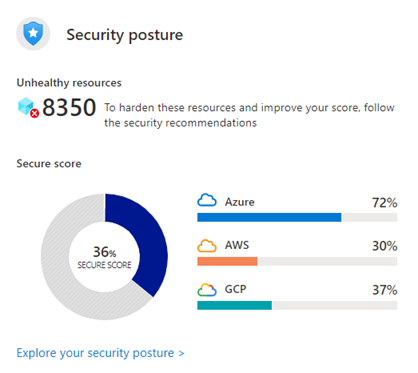

Image Source: Azure
To address security issues and improve your score, check the Defender for Cloud recommendations page and implement the remediation steps for each issue.
Recommendations are broken down into “security controls”. Each control is a logical grouping of related security advisories related to a vulnerable attack surface. The Secure Score will only increase if you resolve all the security issues for a single resource within a control.
The Recommendations page looks like this. Note that it also shows you how each control contributes to the overall Secure Score. This can guide you in prioritizing remediation:
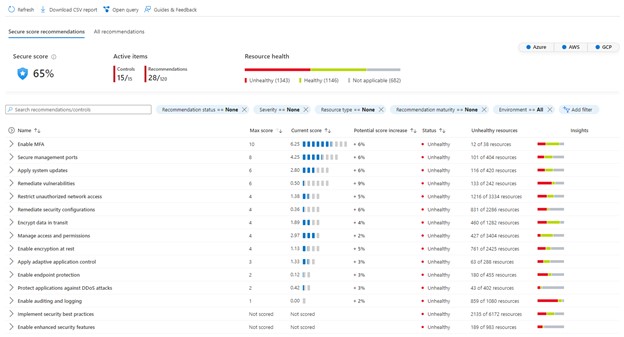

Image Source: Azure
Resource Security Hygiene
In this section, you can discover security hygiene issues affecting your resources. Issues are flagged as low, medium, or high severity based on their potential impact on organizational security. For some issues, you can use Quick Fixes to have Microsoft Defender for Cloud fix the issue automatically.

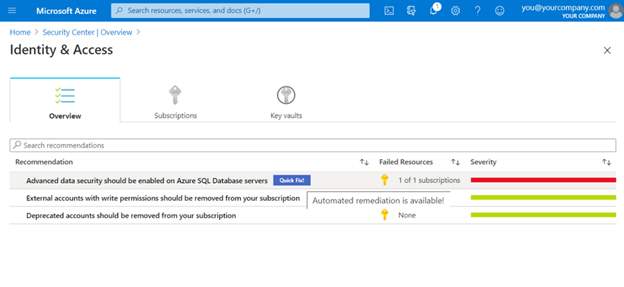
Image Source: Azure
Threat Protection
Microsoft Defender for Cloud can proactively detect and remediate threats to resources and workloads in Azure. In the Threat Protection section of the interface, you can see where attacks might occur and how they will affect your resources. This allows you to conduct better investigations and respond to threats more effectively.
Microsoft Defender for Cloud is natively integrated with Microsoft Defender for Endpoint. Systems running Linux or Windows receive security advisories that can be used to harden their security mechanisms.
You can also use adaptive application controls to make Microsoft Defender for Cloud aware of the types of applications running on endpoints. This makes it possible to examine these applications using threat intelligence and provide insights such as unsafe or unapproved applications running on specific cloud resources.
Networking Security
Microsoft Defender for Cloud continuously monitors your environment based on cybersecurity best practices. Microsoft Defender for Cloud provides alerts and recommendations to help you understand potential security risks and how to best address them.
Defender for Cloud provides the network map, shown below, which can help you understand the health of your Azure network and fix identified issues.
You can use the network map to view the network topology of Azure workloads and the connections between virtual machines, virtual networks, and subnets. Use the map to drill down to specific resources and see detailed recommendations.

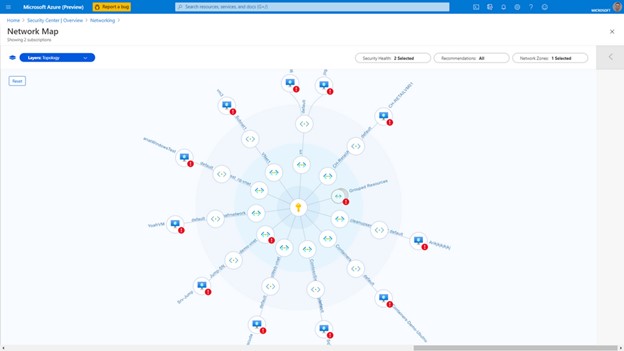
Image Source: Azure
Conclusion
In this article, I explained the basics of endpoint security, and how you can secure endpoints in the Azure cloud using Microsoft Defender for Cloud:
- Secure Score—a unified score showing endpoint security status across your Azure account.
- Resource Security Hygiene—scores for individual Azure endpoints, letting you see specific recommendations for improving security.
- Threat Protection—alerts on threats affecting endpoints, which could indicate a security breach.
- Networking Security—alerts that help you understand the health of Azure networks and fix identified issues.
I hope this will be of help as you improve the security posture of your endpoints in Azure.



